Huawei router vulnerable malware "O...
28
01
Huawei router vulnerable malware "Okill / Satori", attacks around the world: "MIRAI" subspecies
Huawei explained that the unresolved vulnerability in Huawei's router was abused by the new IoT malware, and Huawei's security information released on December 22.
At CHECK POINT SOFTWARE TECHNOLOGIES, a security company that discovered vulnerabilities, this malware is named "OKIRU" (aka SATORI).Some are also called "Okiku".
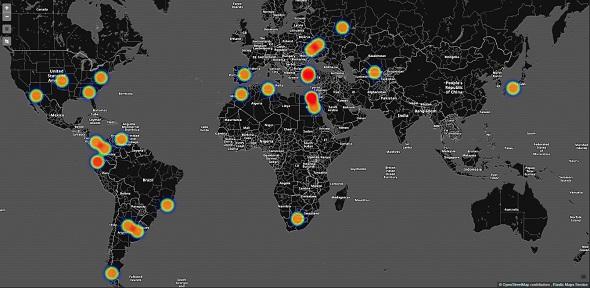
According to CHECK POINT's blog, suspicious behavior was detected on November 23, 2017, and in detail it found that there were attacks that hit the unknown vulnerabilities of "Huawei HG532" around the world.。
Malware OKIRU, which was used for attacks, was a variant of the IoT malware "MIRAI" that caused a large -scale attack in 2016.The implementation of the standard "TR-064" used for devices and firmware updates in Huawei HG532 has a vulnerability, and it turns out that remote attackers may be able to execute any code.。Okiru abused this vulnerabilities.
Huawei HG532の脆弱性を突く攻撃が、世界各地で発生していた(出典:Check Point Software Technologies)According to CHECK POINT, this attack seems to be involved in amateur hackers named "Nexus Zeta".The person said in a hacker forum, asking for advice on how to create a new attack tool."Even an immature hacker combines a leaked malware code with an abuse and thin IoT security can lead to dangerous results," CHECK POINT explains.
Huawei was contacted by CHECK POINT to confirm the vulnerability of HG532.As a countermeasure to prevent abuse, we are calling for the setting of the built -in firewall function and the default password change.
* Editor's note ... "HUAWEI HG532" is a product that has not been released in Japan (12/27 13:45)